Images
Manage container images stored on nodes
6 minute read
Trustgrid nodes support running Docker containers which allows for ease of deployment across an organization. Any Docker container is supported with the exception of containers that require root level access.
The container can be attached to both the local and virtual network space which allows both local and remote resources to communicate with the container. For example an API could be deployed on a Trustgrid Gateway which sends API Calls via the virtual network space to a container running on a Trustgrid Edge Node. The API call could then be translated to make a call to a database running on the local network and passed back up to the gateway host.
Before adding a container to a node, push an image to your repository.
Reading and managing containers requires node-exec::read and node-exec::modify permissions, respectively. Executing a container requires node-exec::compute permission.
Navigate to Container Management under Compute on a node or cluster.
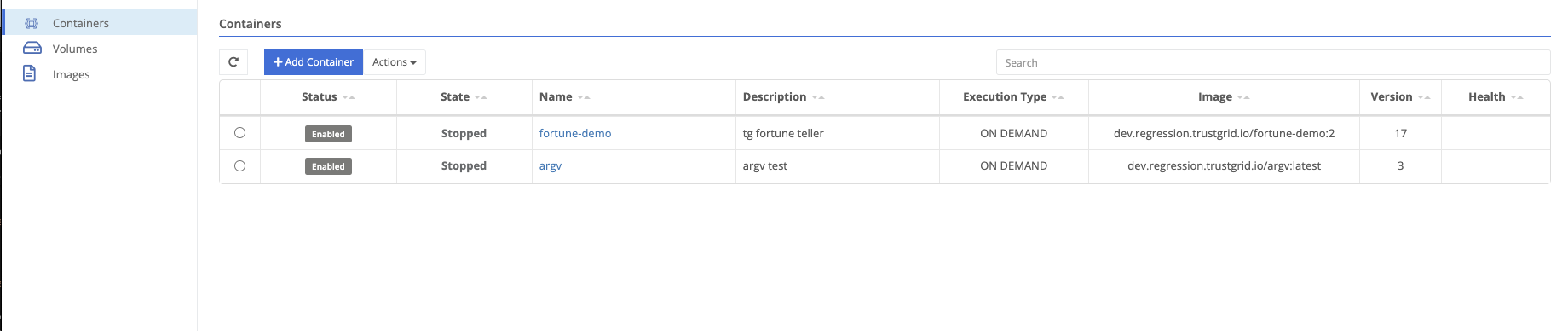
Here you can add, enable, disable, delete, and import a container.
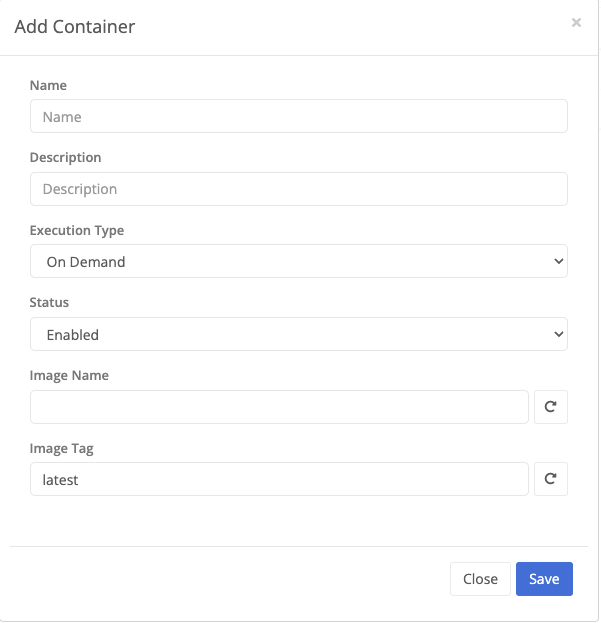
| Field Name | Description | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| Name | The name of the container. | ||||||||
| Execution Type | A container can be deployed as one of three types.
| ||||||||
| Status | Only enabled containers will run. | ||||||||
| Image Name | The name of the image to execute. | ||||||||
| Image Tag | The image tag to execute. |
Navigating into a container, the overview section allows editing basic information about the container’s execution environment.
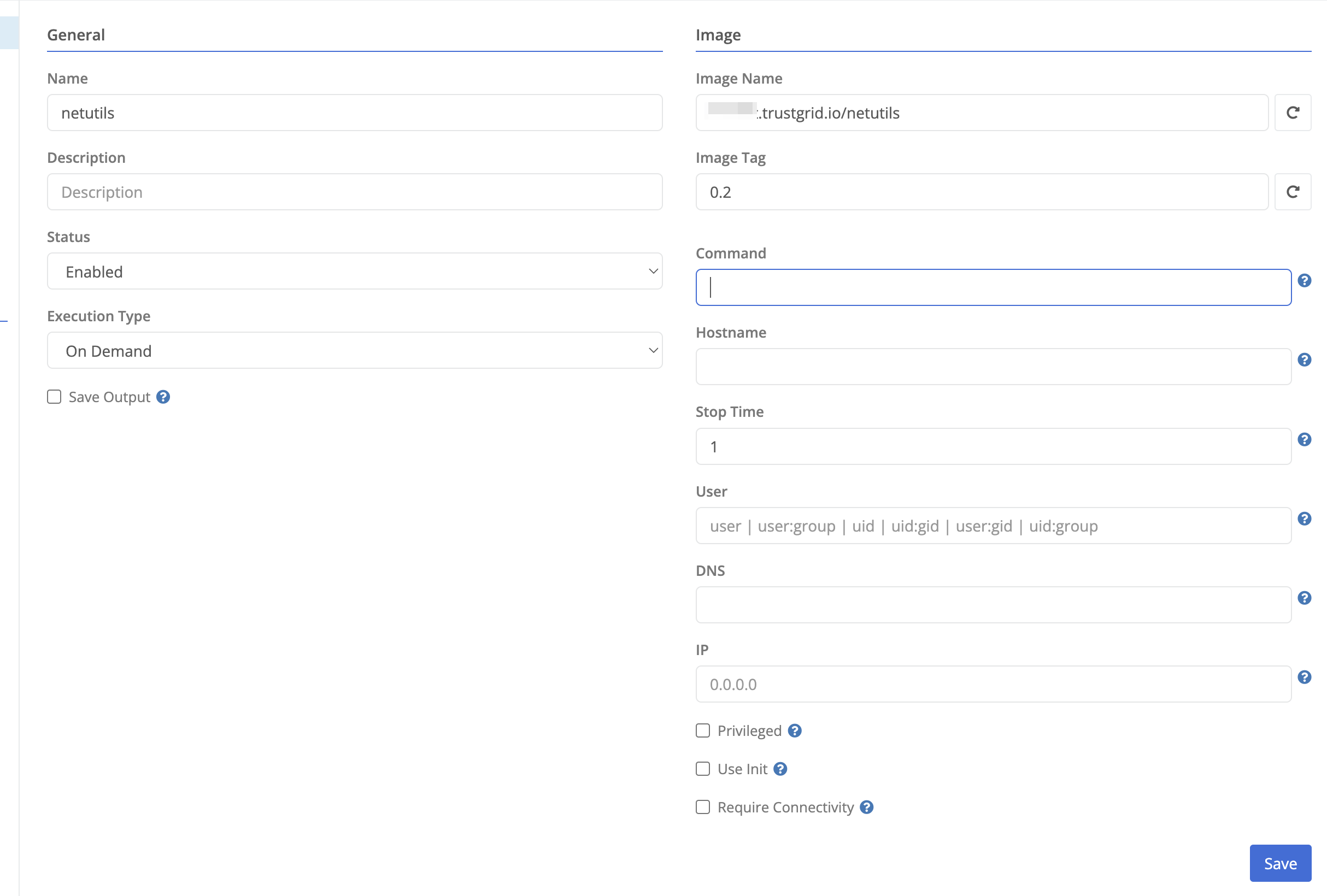
In addition to the fields above, you can modify the below optional fields after saving the new container configuration.
| Field Name | Description |
|---|---|
| Save Output | Persist standard output/standard error to the Trustgrid cloud for analysis. It is the customer’s responsibility to ensure no privileged information is included in the output. If in doubt, do not utilize this feature. |
| Command | The command to execute inside the container. This overrides the start command configured by the dockerfile used to build the image and can be useful for troubleshooting. |
| Hostname | The hostname set inside the container. Defaults to the the node name. |
| Stop Time | The grace period (in seconds) to allow a container to stop before killing it. Defaults to 30 seconds. |
| User | Sets the username or group or uid or gid in the container. |
| DNS | Configures the container to utilize the specified DNS server for resolution. By default the container uses a local resolver managed by the node software that can resolve other containers by name and will forward to the node’s configured DNS servers for external resolution. |
| IP | Configures the container to use the specified IP address. The IP address needs to be in the 172.18.0.0/16 network and cannot be 172.18.1.2. By default this is assigned dynamically in that network. |
| Privileged | Grant the container extended privileges. Best practice would be to utilize linux capabilities to grant the least privileges needed to run the container. |
| Use Init | Use an init process inside the container as PID 1. This ensures responsibilities of an init system are performed inside the container (e.g., handling exit signals). |
| Require Connectivity | Ensures that the container will not start if it has encrypted volumes and is unable to reach the control plane. |
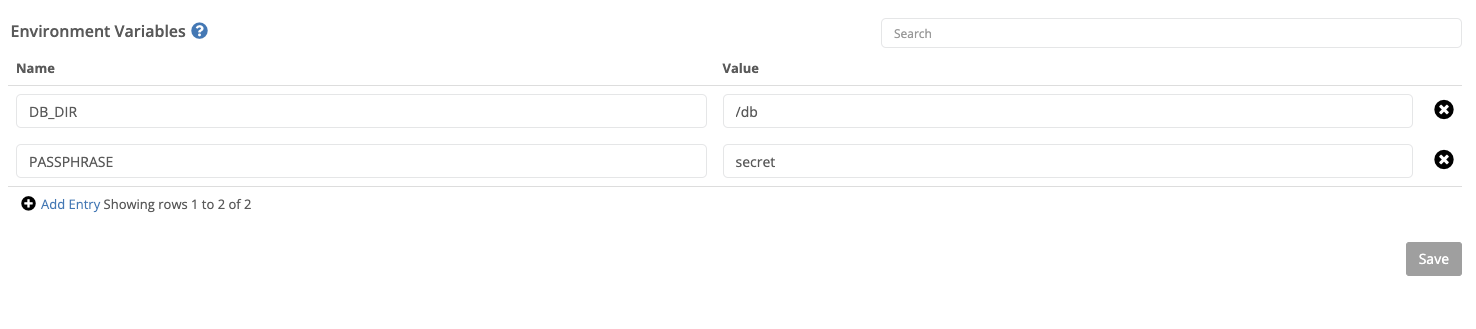
Environment variables can be added to a container to provide configuration information to the container at runtime.
The networking section allows you to configure the container’s VRF, its port mappings, and its virtual networks and interfaces.
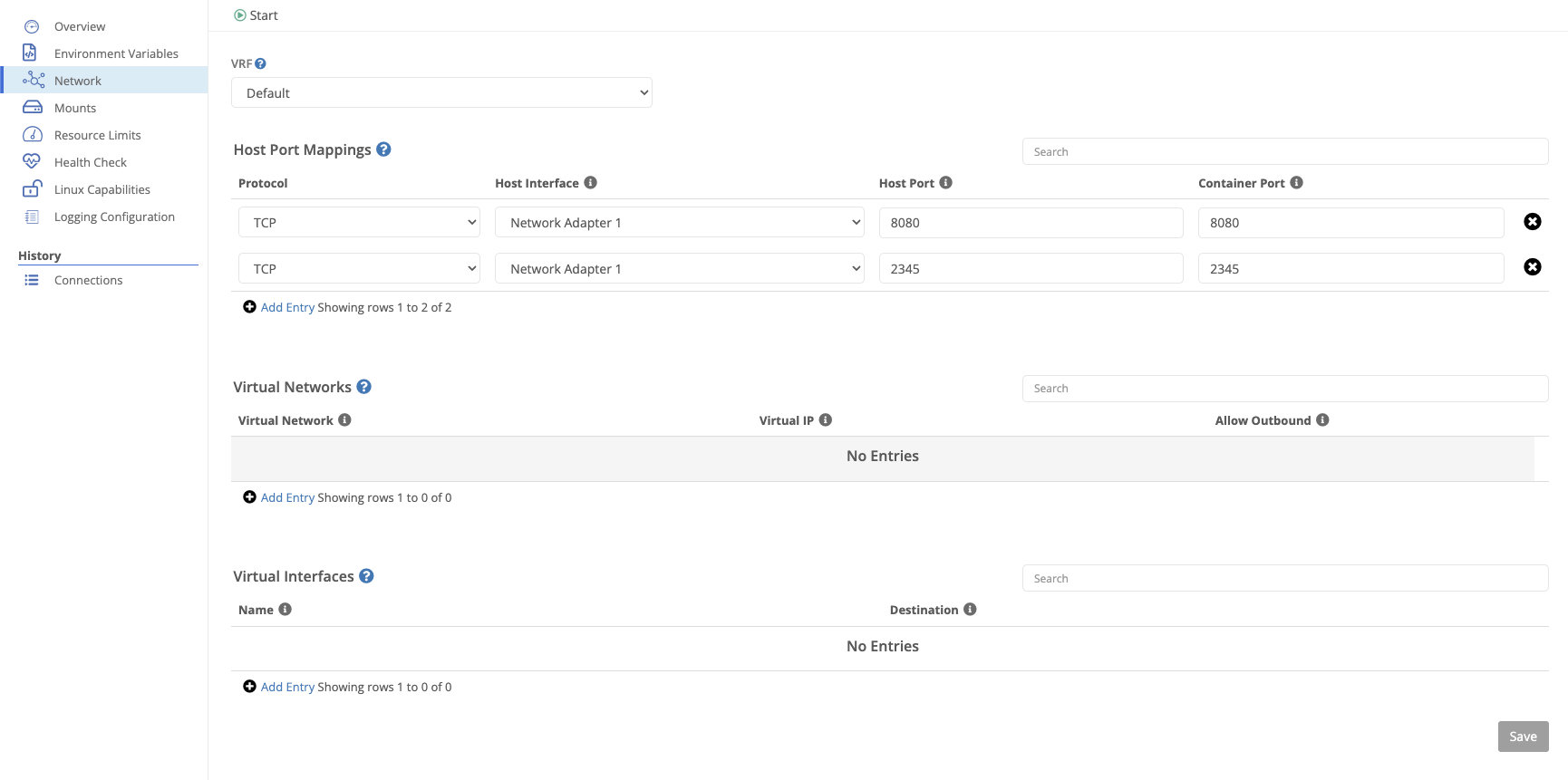
Host port mappings allow you to expose a port on the host to the container. This is useful for exposing a service running in the container to the local network.
| Field Name | Description |
|---|---|
| Protocol | The protocol to listen for. If not specified, all traffic is forwarded to the container. |
| Host Interface | The host interface to listen on. |
| Host Port | The host port to listen on. |
| Container Port | The container port that will receive the mapped traffic. |
Attaching a virtual network to a container allows virtual network traffic to reach it.
| Field Name | Description |
|---|---|
| Virtual Network | The virtual network to attach. |
| Virtual IP | The virtual IP to assign to the container. |
| Allow Outbound | Whether the container should be allowed to make outbound connections into the virtual network. |
A virtual interface can be mapped to a container to forward all traffic.
| Field Name | Description |
|---|---|
| Name | The virtual interface name. |
| Destination | The interface destination inside the container. |
Mounts allow a container to persist data either as an externally defined volume, or a bind mount of the node’s filesystem.
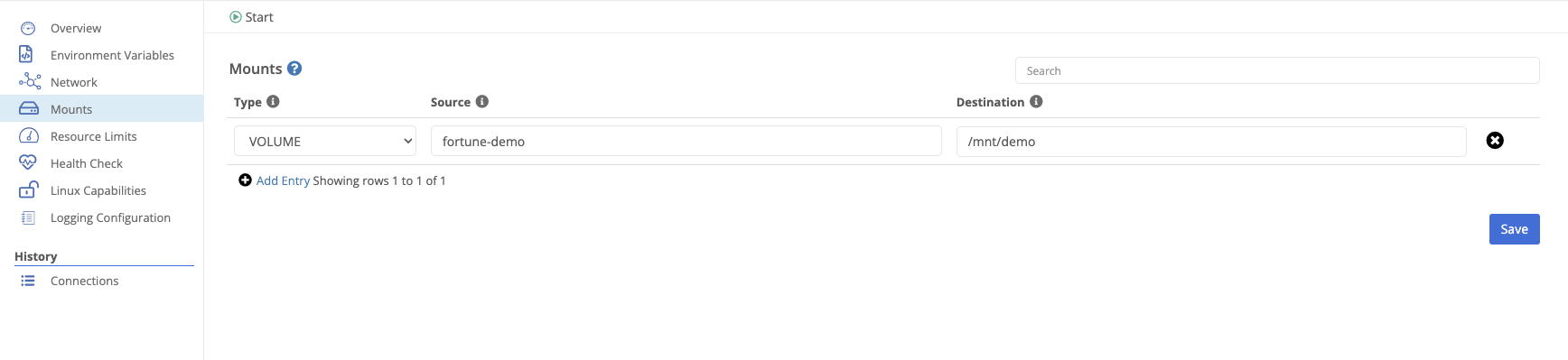
| Field Name | Description |
|---|---|
| Type | Either BIND or VOLUME. For type VOLUME, the mount must reference an existing volume. |
| Source | For volumes, the name of the volume. For bind mounts, the path on the node’s filesystem. |
| Destination | The mount location inside the container. |
Containers can be restricted to limit the amount of resources they can consume from the host.
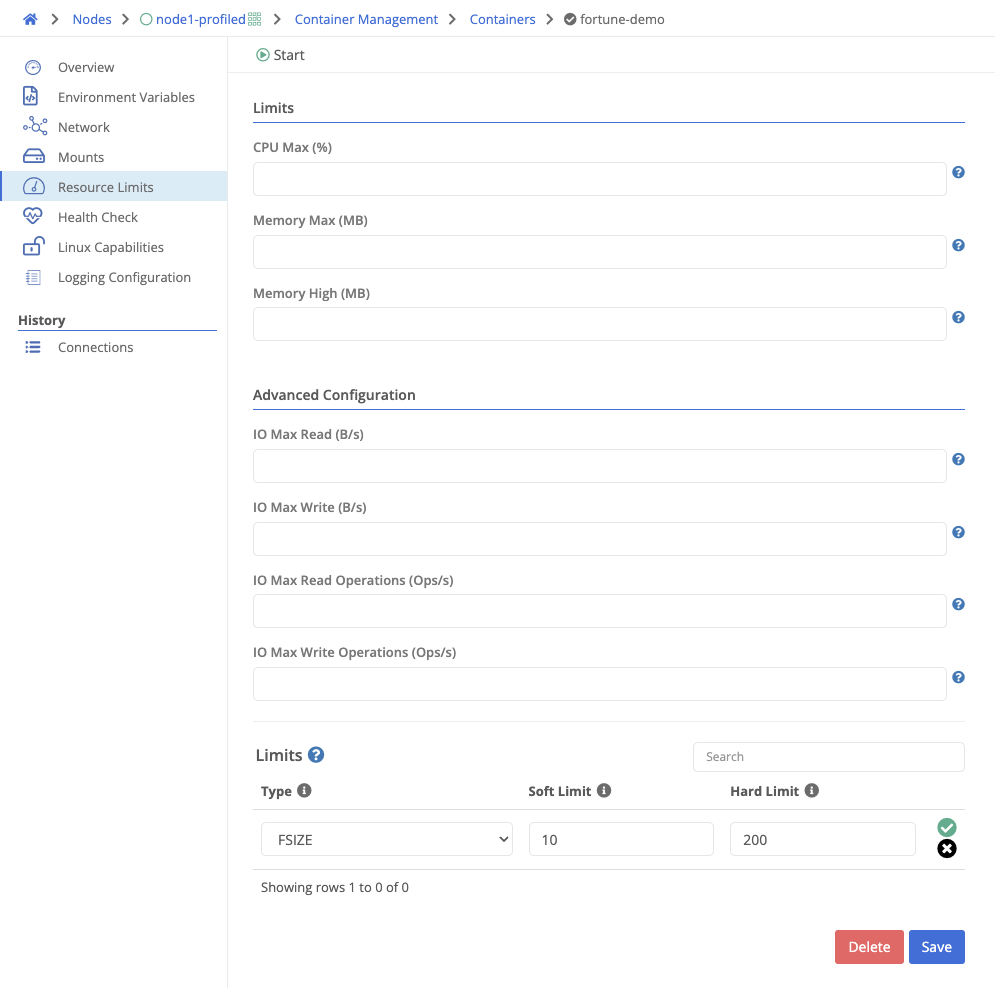
| Field Name | Description |
|---|---|
| CPU Max % | Maximum CPU allocation. Default is 50%. |
| Memory Max (MB) | Hard limit for RAM allocation. Default is 50% of the host’s memory. |
| Memory High (MB) | Soft limit for RAM allocation. Cannot exceed hard limit. Default is 45% of the host’s memory. |
| IO Max Read (B/s) | Max allowed bytes per second of IO reads. Disabled by default. |
| IO Max Write (B/s) | Max allowed bytes per second of IO writes. Disabled by default. |
| IO Max Read Operations (ops/s) | Max allowed IO read operations per second. Disabled by default. |
| IO Max Write Operations (ops/s) | Max allowed IO write operations per second. Disabled by default. |
Linux ulimits can be set for each container. Supported ulimits are:
A health check can be configured to monitor the container’s health. If the health check fails, the container will be restarted.
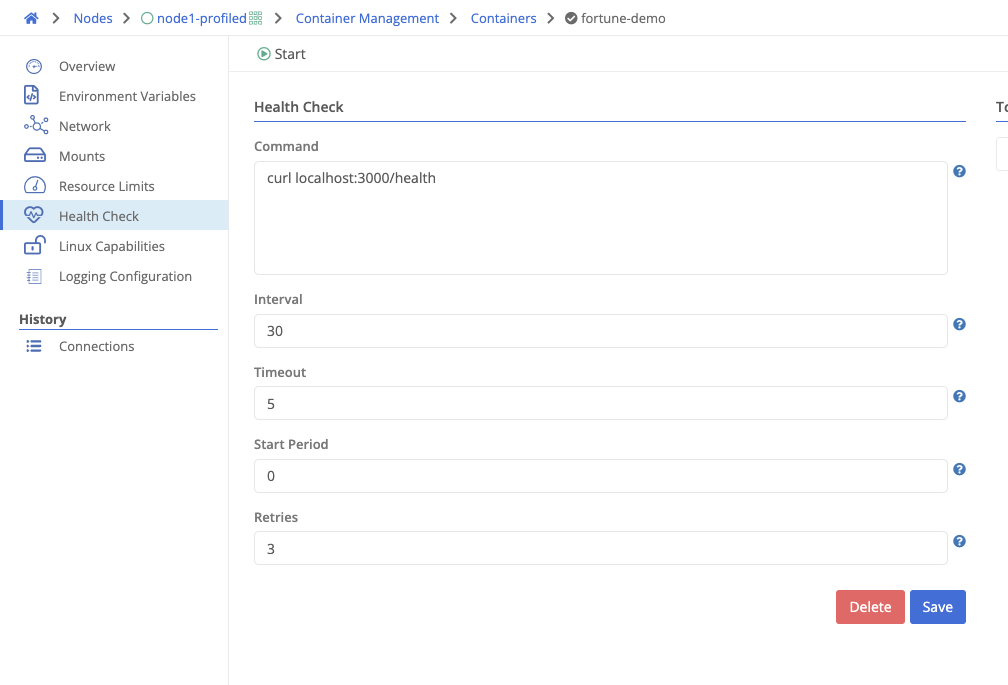
| Field Name | Description |
|---|---|
| Command | The command to run. A non-zero return code indicates a health check failure. |
| Interval | The frequency (in seconds) to run the health check. |
| Timeout | How long (in seconds) to wait for the health check to complete. A timeout is considered a failure. |
| Start Period | Grace period (in seconds) during container startup before health checks should start. |
| Retries | Number of allowed health check failures before marking the container unhealthy. |
Linux capabilities can be added to or removed from a container, allowing fine-grained control over kernel-level features and device access.
Log files (when persisting container output) are rotated based on a size threshold.
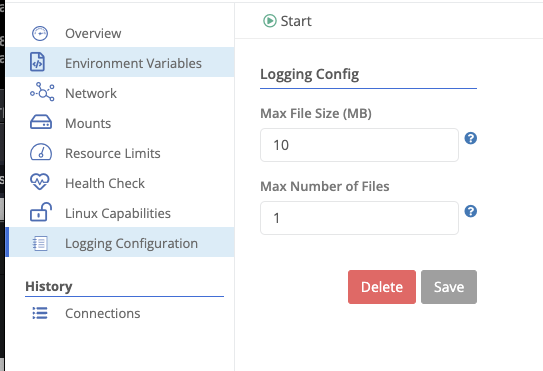
| Field Name | Description |
|---|---|
| Max File Size (MB) | The maximum size (in MB) of a log file before it is rotated. |
| Max Files | The maximum number of log files to keep. |
Manage container images stored on nodes
Configure volumes on nodes for use by containers for persistent storage
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.