WireGuard ®
2 minute read
Nodes may enable a WireGuard server to expose the virtual network to WireGuard clients.
Configuration
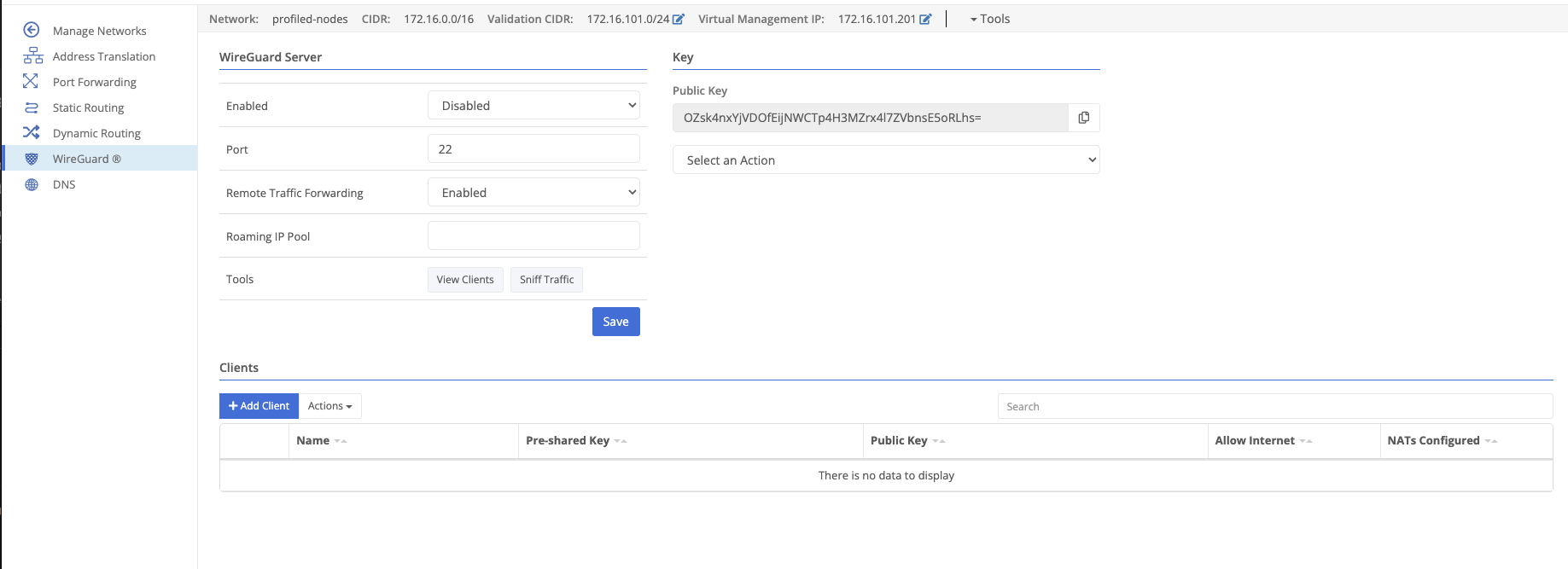
Key Management
Clients will need the server’s public key to connect. This can be generated (using the Regenerate action) or can be derived from the private key (imported using the Import action).
Clients
Clients must be added before they can connect.
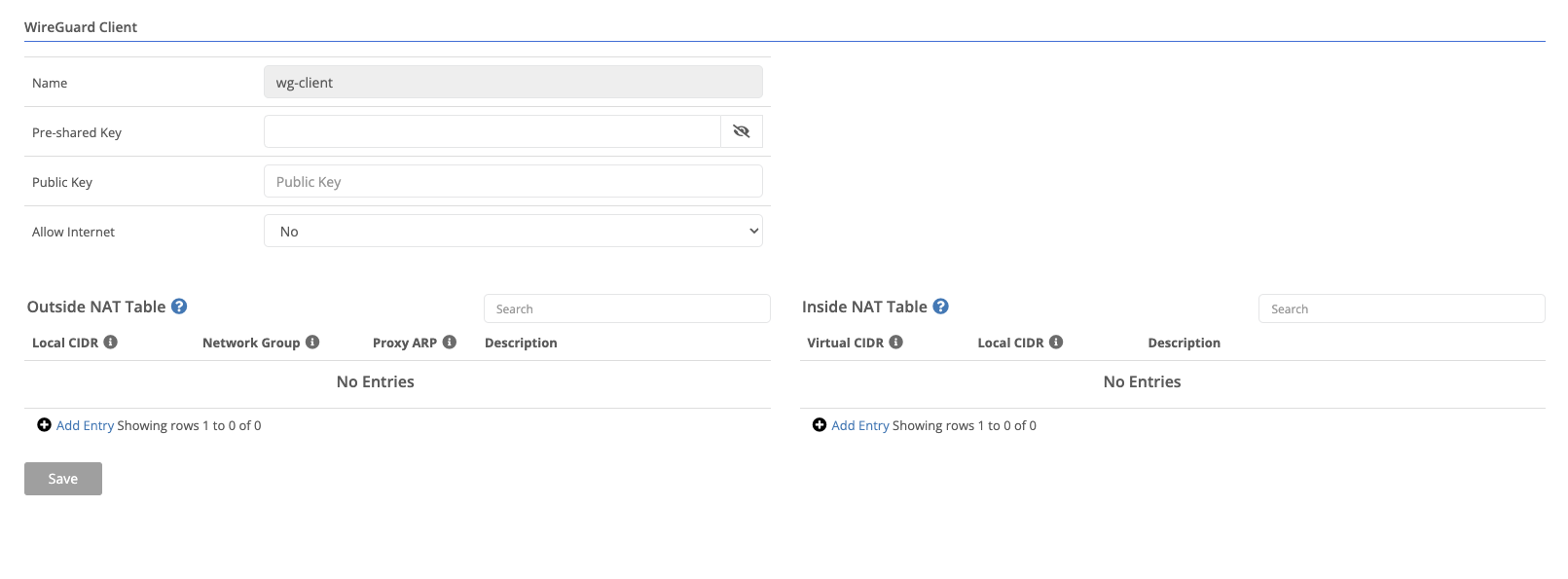
Each client will need to generate their own private and public key. Most WireGuard clients provide tools to do this.
An inside NAT should be created to map the client’s local IP to an IP on the virtual network. The virtual network CIDR should not be a part of any existing routes in the domain. The IP should be included in an outside NAT network group, so that an ACL can allow the traffic.
An outside NAT should be created that includes the virtual network used on the gateway side.
“WireGuard” is a registered trademark of Jason A. Donenfeld.
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.