Azure CLI (az) Deployment
Details how to deploy a Trustgrid appliance and related resources using the Azure CLI (az) commands.
5 minute read
| Requirement | Description |
|---|---|
| Disk Size | At least 30 GB |
| Interfaces |
|
| CPU & RAM | See Instance Type below for recommendations |
Trustgrid has validated using the B-series burstable - Azure Virtual Machines instance type.
VPN throughput is tied to CPU the recommended size depends on roles, expected throughput.
One WAN interface with a public IP and one LAN interface on a private subnet. The nodes will need to be able to route to all required hosts/applications that need to communicate across the Trustgrid virtual network.
The LAN interface needs to have IP Forwarding Enabled in order to forward the traffic across the tunnel.
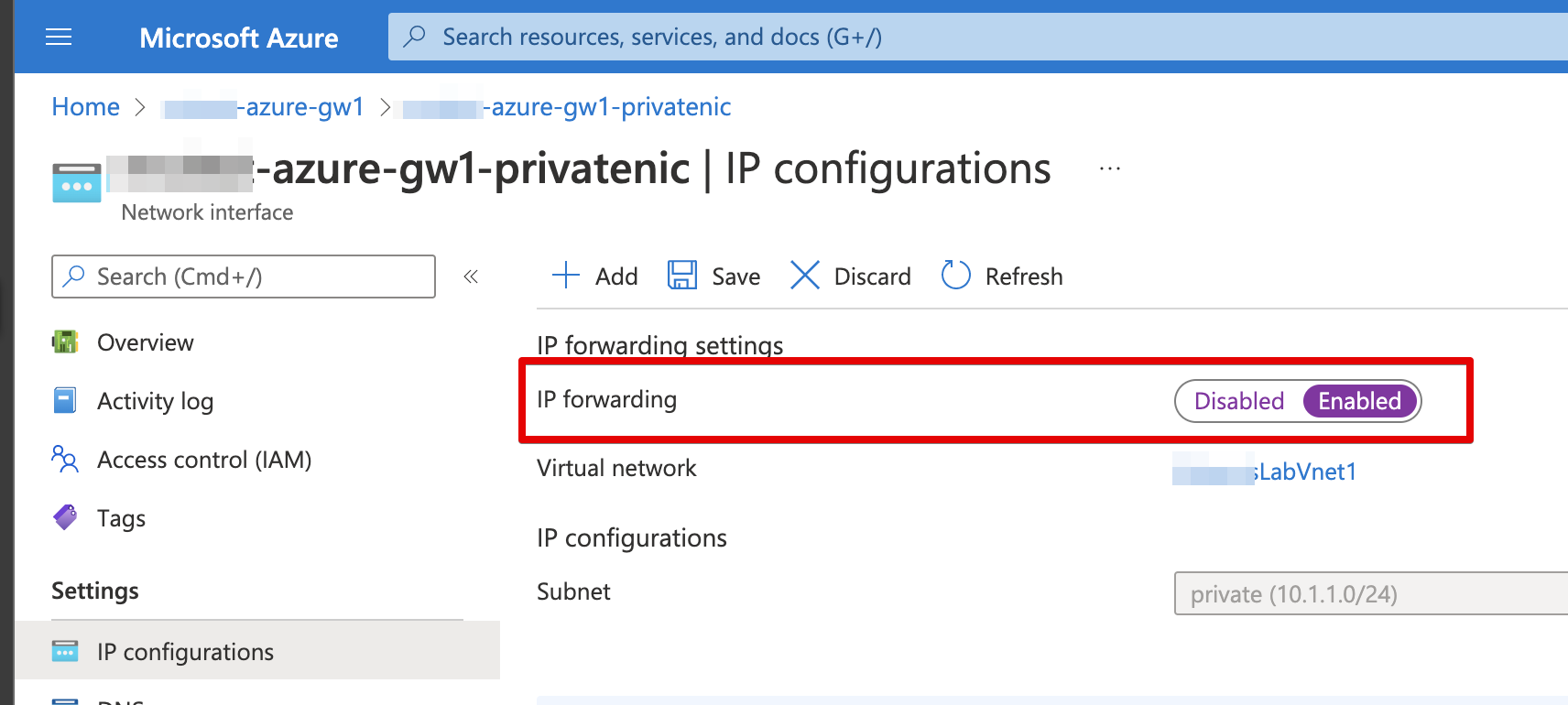
See Azure virtual network traffic routing.
The Trustgrid official community image, trustgrid-node-2204-prod, in the public gallery trustgrid-45680719-9aa7-43b9-a376-dc03bcfdb0ac is currently published in the following regions. If you need to deploy in another region, please contact Trustgrid support. If you are not a direct customer of Trustgrid, please check with your vendor that is utilizing Trustgrid to have them contact support.
| Region Display Name | Region Name |
|---|---|
| East US | eastus |
| East US 2 | eastus2 |
| Central US | centralus |
| North Central US | northcentralus |
| South Central US | southcentralus |
| West US | westus |
| West US 2 | westus2 |
| West US 3 | westus3 |
For gateways:
For edge nodes:
For all clustered nodes:
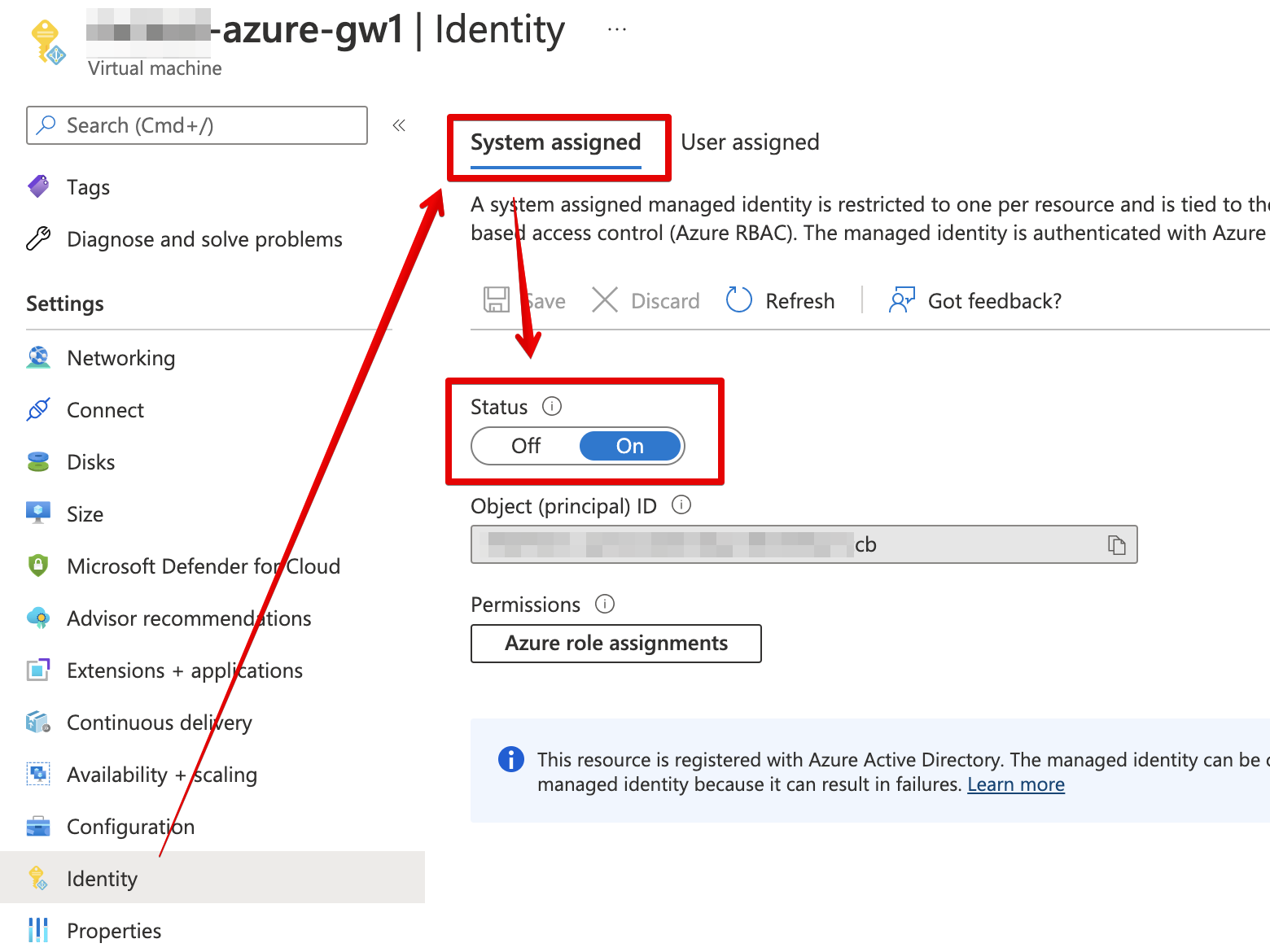
One of more Virtual Machines will need to be deployed into the target Azure subscription to act as the Trustgrid nodes using the official community image. Then the remote registration process can be used to activate the nodes in the Trustgrid portal.
If the Site Tech is not part of the organization that is a Trustgrid’s direct customer, Trustgrid’s professional service team will need documented approval from that customer before proceeding with assisting in the deployment.
Documentation Coming Soon for…
Trustgrid supports two methods for supporting high availability networking connectivity via clustered Trustgrid nodes in Azure. These methods can be used together or independently.
| Method | Description | Common Use Cases |
|---|---|---|
| Route failover | Publishes routes to the Azure route table associated an interface or specified route tables. Automatically adjusts the Next hop IP address to point to the active node. |
|
| IP failover | Assigns a floating IP address to the interface of the active Trustgrid node. |
|
1 Route based failover requires the nodes to have correct Azure permission to modify each route table. Environments with many route tables would have to grant permission to the containers (resource groups, subscriptions) for each table which makes maintaining least-privilege access difficult.
Details how to deploy a Trustgrid appliance and related resources using the Azure CLI (az) commands.
IP Failover for Azure appliances
Route failover for Azure appliances
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.