Sniff Traffic Interface Tool
Monitor network traffic on a local interface in realtime
2 minute read
The Sniff Traffic tool allows you to monitor traffic on a local network interface in realtime within the Trustgrid portal. Only the header information such as source and destination IPs, TCP flags, sequence numbers, etc. are displayed.
Using Sniff Interface Traffic
- Login to the Trustgrid portal and navigate to the Node from which you want to view traffic.
- Select
Interfacesunder theNetworksection. Then from the dropdown select the interface whose traffic you want to monitor.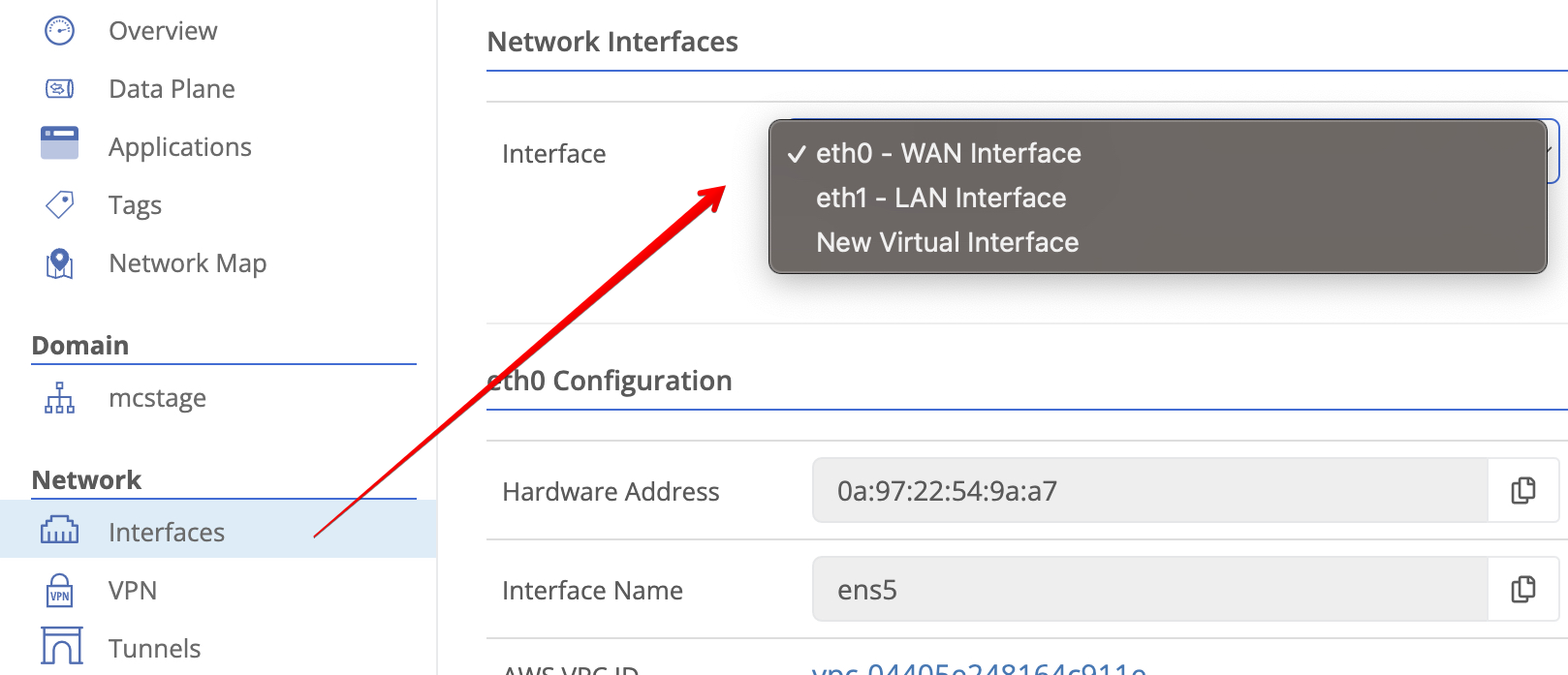
Selecting the desired interface - Click the Sniff Traffic button.
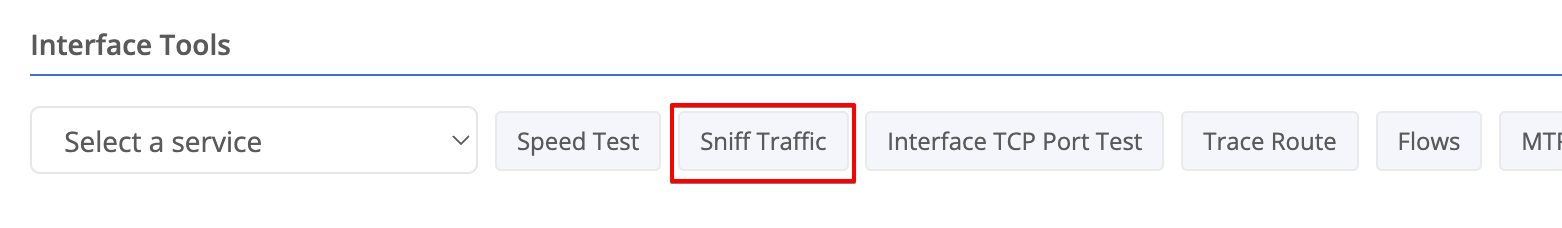
- Set the Interface and Filters to match the traffic you wish to monitor.
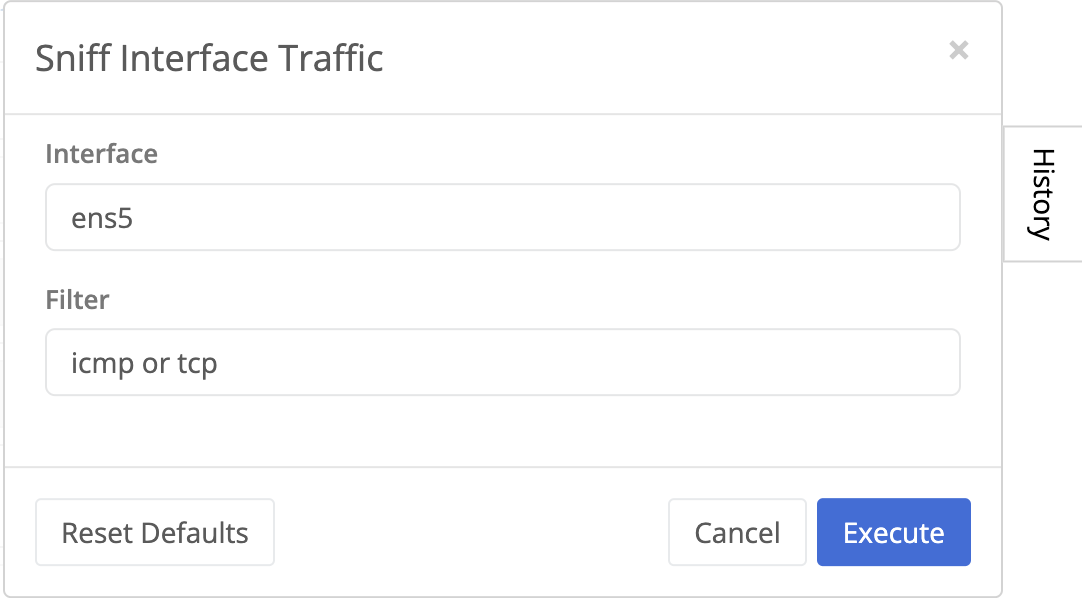
Field Name Description Interface The interface name. This should be auto-populated with the interface selected above. If not, either click the Reset Default button or erase the interface name and select from the list. Filter The tool utilizes TCPDump filtering syntax, which can help isolate interesting traffic. The below filter would show only ICMP and TCP traffic. See the useful filters below for a quick introduction. - Click
Executeto view the captured traffic
Example output of sniffing interface traffic
Useful Filters
The below filters can be combined using “and” & “or” without quotes
- You can filter based on protocol such as “tcp”, “udp”, or “icmp” without quotes
- Best practice is to filter for what you want to see rather than filter out what you don’t want to see
- To see only traffic for a specific host use “host x.x.x.x” with the IP address in place of the x.x.x.x
- To see only traffic for a specific port use “port XXXX” replacing the XXXX with the desired port number
- If capturing traffic on a clustered node, you should filter out the cluster port traffic. Typically port 9000 or 1975. E.g.,
not port 9000 - If capturing on the ETH0 - WAN Interface, you should filter out traffic to both Trustgrid’s network (35.171.100.16/28) and your data plane gateways’ network or public IP. You’ll need to identify the actual network or IPs. E.g.,
not net 35.171.100.16/28 and not net X.X.X.X/Xornot net 35.171.100.16/28 and not host X.X.X.X.
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.