Sniff Virtual Traffic
3 minute read
Summary
This tool allows you to monitor the traffic flowing over a VPN tunnel by “sniffing” inside the tunnel. This allows traffic to be viewed after NATs have been applied and confirm traffic is routed to or from the expected node.
Usage
This tool is accessed on a node’s detail page under the VPN panel. Select the desired attached virtual network (note: if only on virtual network is present it will be selected by default) and click the “Tools” button in the top right.

Once launched, you will be prompted to provide any filters to limit the traffic displayed. The default is to show all traffic on that virtual network tunnel.

| Field Name | Description |
|---|---|
| Peer(s) | Use this field to filter for traffic only between the current node and the listed peer. |
| Protocol(s) | Filter to specified network protocol(s): any, tcp, udp, or icmp |
| Host(s) | Filter to see traffic matching the specified virtual IP address(es) |
| Port(s) | Filter to see traffic matching the specified ports. This will match either a destination or source port. The operator on the left allows for matching based on:
For ICMP, this field does not apply. |
| TCP Flags | Only applies to TCP traffic. It can filter based on the following flags:
More than one flag can be specified, such as “S.” to show only traffic with SYN or ACK flags set. |
Output
Below shows sample output from using this tool to monitor traffic on a virtual network between two nodes:
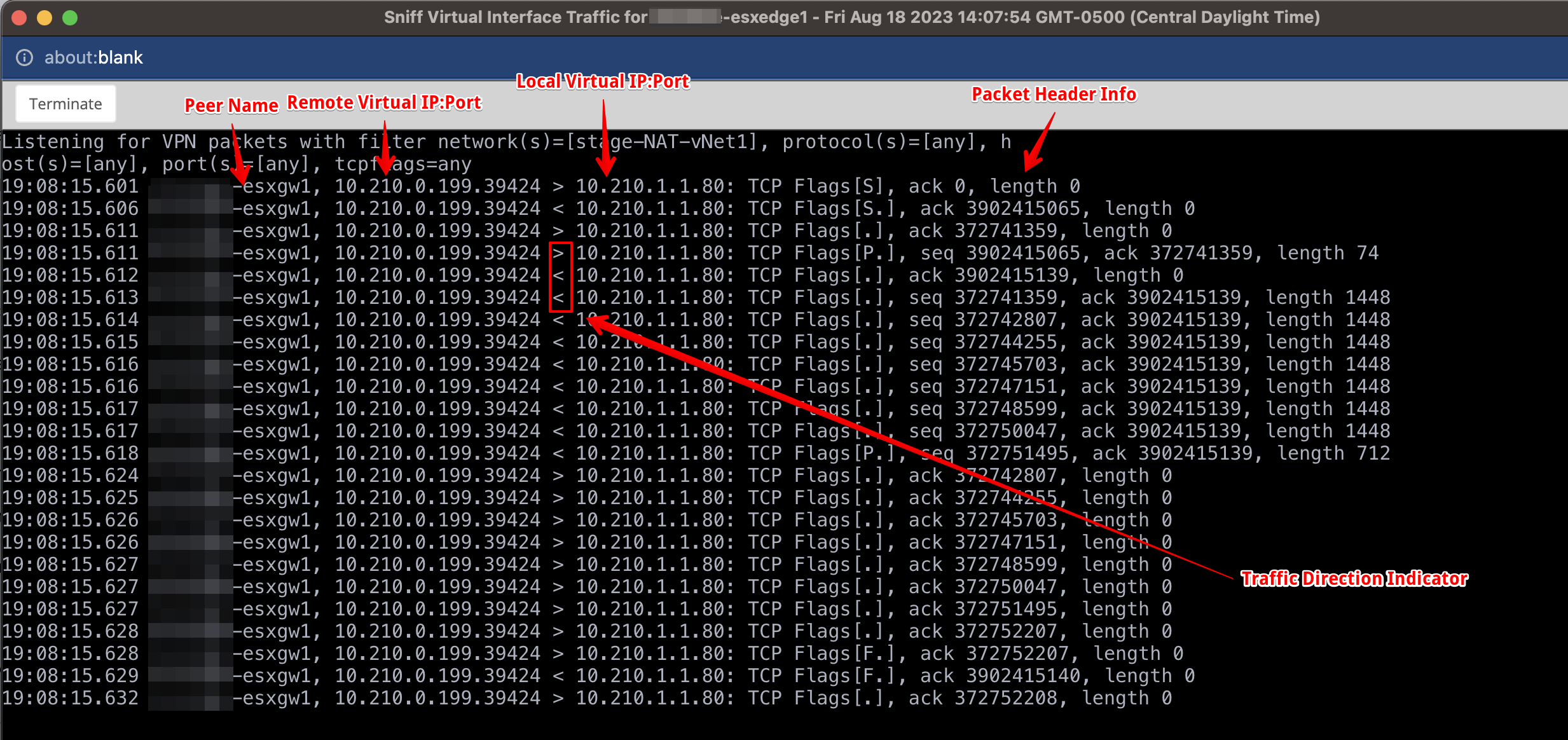
The output includes the following data for each packet:
| Field Name | Description |
|---|---|
| Timestamp | The time the packet was seen |
| Peer | The source or destination node of the packet |
| Remote Virtual IP:Port | The virtual IP address and port of the source or destination remote endpoint |
| Direction Indicator | The symbols indicating if the packet was sent or received by the local node:
|
| Local Virtual IP:Port | The virtual IP address and port of the local endpoint |
| Packet Header Information | Additional metadata about the packet such as:
|
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.